Friday 27 July 2012
JUNIPER 1 Days e-book
JUNIPER
root@juniper1# set class super-user >> set user dengan port dan level user
#set system >>>>> hierarcy as a reminder of basic settings that you can configure
#set system root-authentication plain-text-password >>>>> set password user
#set system services ssh root-login deny >>>>> Strengthen security by only allowing root access from the console port:
#set system host-name juniper1 >>>>> Set hostname
#set interfaces lo0 unit 0 family inet address 192.26.0.110/32 >>> set int looback
#set system backup-router 172.26.31.1 destination 172.16.0.0/12 >>> system backup
#set system name-server 172.26.27.2 >>> set name-server DNS
#set system domain-name enterprise.com >>> domain set
#set system domain-search [enterprise.com department.enterprise.com] >>> searching domain ip address
#show host 172.26.27.44 >>> used configured hostname resolution to the ip address
44.27.26.172.in-addr.arpa domain name pointer juniper1.enterprise.com.
#show host juniper1
juniper1.enterprise.com has address 172.26.27.44
#root@juniper1> set date 200901011200.00 >>> set time
The date is in the form (YYYYMMDDhhmm.ss)
#set system ntp boot-server 172.26.27.4 >>> time boot server cinchornyses
#set system ntp server 172.26.27.4 >>> keep ti device synchronize with priodic updates
#set system time-zone Europe/Amsterdam >>> zone time
#set date ntp 172.26.27.4
7 Apr 10:32:27 ntpdate[4544]: step time server 172.26.27.4 offset -0.000565 sec
#show system uptime >>>>
#show ntp associations
#show ntp status
#show chassis hardware
#show configuration interfaces ge-0/0/1
#show configuration interfaces ge-0/0/1 | display set
#set system login message “ Welcome \n to \n JUNOS Training\n “
$ ssh juniper1
Welcome
to
JUNOS Training
root@juniper1’s password:
#set system login message “WARNING: Unauthorized access is an offense”
#set system login announcement “Maintenance scheduled 11PM to 2AM tonight”
#edit system login
#edit user jadmin
[edit system login user jadmin]
#root@juniper1# set full-name "Juniper Network Administrator"
edit system login user jadmin]
#root@juniper1# set uid 1250
[edit system login user jadmin]
#root@juniper1# set authentication plain-text-password
New password: ####
Retype new password: ####
n super-user: all permissions
n operator: clear, network, reset, trace, and view permissions
n read-only: view permissions
n unauthorized: no permissions
[edit system login user jadmin]
#root@juniper1# set class super-user
#set system login class netops
#set system login class netops permissions all
How to start the configuration for authentication by a RADIUS server:
Use the following steps to start the set up of user authentication by a
RADIUS server. Complete the set up with steps 3 and 4 below
#set system radius-server 172.26.27.5
2. You can also include a shared secret in the command statement and,
if necessary, the port number:
#set system radius-server 172.26.27.5 port 1845
#set system radius-server 172.26.27.5 secret Jun1p3r
How to start the configuration for authentication by a TACACS+ server:
Use the following steps to start the set up of user authentication by a
TACACS+ server. Complete the set up with steps 3 and 4 below.
1. Enter the TACACS+ configuration statement:
#set system tacplus-server 172.26.27.6
#set system tacplus-server 172.26.27.6 port 49
#set system tacplus-server 172.26.27.6 secret Jun1p3r
#set system authentication-order [ radius tacplus password ]
#set system login user adminjlk class super-user
#set system login user remote class super-user
Corret userlogin
#root@juniper1> show log messages
Apr 22 13:38:58 juniper1 sshd[17859]: Accepted password for adminjlk from 172.30.48.10
port 61729 ssh2
no user login
Apr 22 13:40:57 juniper1 sshd[17873]: Failed password for username from 172.30.48.10
port 64844 ssh2
Tuesday 17 July 2012
Malam 17 Juli 2012
01:19
2 comments
Sekarang adalah malam selasa dinihari. dimana tadi pagi saya berangkat dari rumah menuju kantor. Jaraknya memang tidak jauh antara Karawang dan Jakarta. Namun perjalanan antara Karwang-Jakarta ini memang waktu sampe 4 jam lebih. Berangkat dari rumah jam 7 pagi. Pergi ke Cikampek pemberhantian pertama, kemudian ke karawang untuk naik bus ARGAMAS ke kampung Rambutan. Dari kampung Rambutan naik busway ke kampung melayu,dari kampung melayu turun di matraman 1 untuk transit dan kemudian dari Matraman 1 ke dukuh atas, dari dukuh atas jalan kaki 15 menit ke kantor. dan nyampe kantor shalat dzuhur terlebih dahulu. Dan standbay dikantor. ya ini perjalanan saya yang memakan waktu hampir 4 jam lebih...
Sebelum berangkat seperti biasa selalu mendapatkan doa dan restu dari orang tua... Cepat sukses nak..!!! cepat selalu umrah dan naik haji... itu yang sering kali saya mendengar dari orang tua.
Sekarang lagi mengerjakan projek MEDIA ALKES (usaha dari kakak). yang design logo saya, yang design banner saya, pokoknya yang berhubungan dengan desain saya. sempat ditawarkan hape samsung, tapi karena teteh gak ada, maka blum dikasih.. mudah-mudahan lebaran dikasih samsung.
Nah.. diperjalan dari Cilamaya-Cikamapek, ketemu sama temen pengajian,
Awalnya diam, tapi saya sudah nebak ini temen saya. dalam hati siapa namanya ya... lupa..
Dia : lung.. mau kemana ? (nama saya Alung klo panggil di kampung, jadi jangan harap ketemu nama abdul di kampung saya... hheehee )
Sy: ia.. mau kerja ..
Dia : masih ingat gak ma saya ? ()
Sy : masih.. siapa namanya ya Fajri ??
Dia : hm.. bukan hayo tebak..
Sy : kerja dimana ??
Dia : Kerja di pencucian di Surkalim.
.........
Sy : saya nitip salam ya ketemen yang ada disana.
Tepat jam 00:00 di kantor kedatang vendor xxx, nah awal dari bagian pertama di DATA CENTER COLOCATION neh.. cuma nemenin keatas saja dan dikasih delivery 24 jam.
Dan nugguin sampe kelar dah neh kayaknya..
Nanti lanjut ceritanya
Lagi baca CISCO LAN SWITCHING AND WIRELESS
^_^
Sebelum berangkat seperti biasa selalu mendapatkan doa dan restu dari orang tua... Cepat sukses nak..!!! cepat selalu umrah dan naik haji... itu yang sering kali saya mendengar dari orang tua.
Sekarang lagi mengerjakan projek MEDIA ALKES (usaha dari kakak). yang design logo saya, yang design banner saya, pokoknya yang berhubungan dengan desain saya. sempat ditawarkan hape samsung, tapi karena teteh gak ada, maka blum dikasih.. mudah-mudahan lebaran dikasih samsung.
Nah.. diperjalan dari Cilamaya-Cikamapek, ketemu sama temen pengajian,
Awalnya diam, tapi saya sudah nebak ini temen saya. dalam hati siapa namanya ya... lupa..
Dia : lung.. mau kemana ? (nama saya Alung klo panggil di kampung, jadi jangan harap ketemu nama abdul di kampung saya... hheehee )
Sy: ia.. mau kerja ..
Dia : masih ingat gak ma saya ? ()
Sy : masih.. siapa namanya ya Fajri ??
Dia : hm.. bukan hayo tebak..
Sy : kerja dimana ??
Dia : Kerja di pencucian di Surkalim.
.........
Sy : saya nitip salam ya ketemen yang ada disana.
Tepat jam 00:00 di kantor kedatang vendor xxx, nah awal dari bagian pertama di DATA CENTER COLOCATION neh.. cuma nemenin keatas saja dan dikasih delivery 24 jam.
Dan nugguin sampe kelar dah neh kayaknya..
Nanti lanjut ceritanya
Lagi baca CISCO LAN SWITCHING AND WIRELESS
^_^
Friday 29 June 2012
Lomba Penulisan Artikel Blog Berhadiah Voucher 8,5 Juta Rupiah
Lomba Penulisan Artikel Blog Berhadiah Voucher 8,5 Juta Rupiah
NetCampus Training Center menyelenggarakan sayembara penulisan artikel blog berhadiah voucher training CCNP senilai 8,5 juta rupiah. Training CCNP dilaksanakan di NetCampus Training Center dengan trainer Pak Samrony Fauzi, CCNA, CCNP, CCIE.
Persyaratan Lomba :
- Judul artikel harus sesuai ketentuan panitia lomba, yaitu : “Kiat Sukses Menjadi Seorang Network Engineer”.
- Minimal jumlah paragraph adalah 4 paragraf dengan setiap paragraf terdapat minimal 3 kalimat.
- Dalam isi artikel tsb setidaknya harus terdapat 3 keyword hyperlink yaitu : training komputer, kursus komputer, dan training ccna yang linknya diarahkan ke situs resmi netcampus : www.netcampus.co.id
- Isi artikel harus mencerminkan judul artikel yang memberikan informasi bagaimana cara menjadi seorang network engineer yang sukses serta merekomendasikan training jaringan komputer di NetCampus Training Center.
- Minimal harus ada 1 gambar ilustrasi di dalam artikel tsb.
- Artikel harus orisinal dan bukan copy paste dari website lain.
- Pendaftaran lomba dimulai sejak tanggal 29 Juni 2012 dan ditutup tanggal 10 September 2012. Penentuan pemenang akan diumumkan pada tanggal 1 Desember 2012.
- Mendaftarkan diri dan artikel Anda melalui form pendaftaran online : FORMULIR ONLINE atau di URL : http://netcampus.co.id/form-pendaftaran-lomba-artikel-blog/
Kriteria pemenang lomba :
- Memenuhi persyaratan yang telah disebutkan diatas.
- Artikel yang ditulis bila di search di mesin pencari google.co.id dengan kata kunci “Kiat Sukses Menjadi Seorang Network Engineer” menempati posisi 1 (pertama). Hasil pencarian di google berdasarkan hasil pencarian yang dilaksanakan di kantor NetCampus menggunakan komputer yang dimiliki oleh NetCampus.
Syarat dan Ketentuan :
- Lomba tidak berlaku bagi staff dan karyawan NetCampus/NetSolution.
- Keputusan pemenang lomba berdasarkan kriteria pemenang lomba tsb diatas tidak dapat diganggu gugat.
- Voucher training CCNP tidak bisa diuangkan namun bisa digunakan oleh pihak ke-3 berdasarkan persetujuan si pemenang.
- Voucher training berlaku 1 (satu) tahun semenjak diterbitkan secara resmi oleh NetCampus. Lewat dari satu tahun voucher dianggap hangus.
Kontak informasi :
- Bila ada pertanyaan yang berkaitan dengan perlombaan penulisan artikel ini, silahkan layangkan email ke : abdulloh@netcampus.co.id atau telp. 021-47884163/68/69.
Thursday 21 June 2012
Install Nagios di Ubuntu 10.04
Nagios (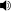 /ˈnɑːɡiːoʊs/) is a popular open source computer system monitor, network monitoring and infrastructure monitoringsoftware application. Nagios offers complete monitoring and alerting for servers, switches, applications, and services and is considered[by whom?] the defacto industry standard in IT infrastructure monitoring. It watches hosts and services, alerting users when things go wrong and again when they get better.
/ˈnɑːɡiːoʊs/) is a popular open source computer system monitor, network monitoring and infrastructure monitoringsoftware application. Nagios offers complete monitoring and alerting for servers, switches, applications, and services and is considered[by whom?] the defacto industry standard in IT infrastructure monitoring. It watches hosts and services, alerting users when things go wrong and again when they get better.
Nagios, originally created under the name NetSaint, was written and is currently maintained by Ethan Galstad, along with a group ofdevelopers actively maintaining both official and unofficial plugins. N.A.G.I.O.S. is a recursive acronym: "Nagios Ain't Gonna Insist On Sainthood",[3] "Sainthood" being a reference to the original name NetSaint, which was changed in response to a legal challenge by owners of a similar trademark.[4] "Agios" is also a transliteration of the Greek word άγιος which means "saint".
Nagios was originally designed to run under Linux, but also runs well on other Unix variants. It is free software, licensed under the terms of the GNU General Public License version 2 as published by the Free Software Foundation.
In a 2006 survey among the nmap-hackers mailing list, 3243 people responded when asked for their favorite network security tools. Nagios came in 67th overall and 5th among traffic monitoring tools. Nmap itself was excluded from the list. Update: The 2011 list has been released and Nagios is listed at #69. [5]
Nagios XI is the new front end that was recently released. It is built on top of the free Nagios Core, and by far the most spohisticated front end available for Nagios Core. It is licensed at a modest price, which includes up to 10 Nagios support calls.
Nagios is Open Source Software licensed under the GNU GPL V2.
- Monitoring of network services (SMTP, POP3, HTTP, NNTP, ICMP, SNMP, FTP, SSH)
- Monitoring of host resources (processor load, disk usage, system logs) on a majority of network operating systems, including Microsoft Windows with the NSClient++ plugin or Check_MK.
- Monitoring of anything else like probes (temperature, alarms...) which have the ability to send collected data via a network to specifically written plugins
- Monitoring via remotely-run scripts via Nagios Remote Plugin Executor
- Remote monitoring supported through SSH or SSL encrypted tunnels.
- Simple plugin design that allows users to easily develop their own service checks depending on needs, by using the tools of choice (shell scripts, C++, Perl, Ruby, Python,PHP, C#, etc.)
- Plugins available for graphing of data (Nagiosgraph, PNP4Nagios, Splunk for Nagios, and others available)
- Parallelized service checks available
- Ability to define network host hierarchy using "parent" hosts, allowing detection of and distinction between hosts that are down and those that are unreachable
- Contact notifications when service or host problems occur and get resolved (via e-mail, pager, SMS, or any user-defined method through plugin system)
- Ability to define event handlers to be run during service or host events for proactive problem resolution
- Automatic log file rotation
- Support for implementing redundant monitoring hosts
- Optional web-interface for viewing current network status, notifications, problem history, log files, etc.
- Data storage is done in text files rather than database.
Nagios Agents
[edit]
NRPENagios Remote Plugin Executor (NRPE) is a Nagios agent that allows remote systems monitoring using scripts that are hosted on the remote systems. It allows for monitoring resources such as disk usage, system load or number of users currently logged in. Nagios periodically polls the agent on the remote system using thecheck_nrpeplugin.[edit]
NRDPNagios Remote Data Processor (NDRP) is a Nagios agent with a flexible data transport mechanism and processor. It is designed with an architecture that allows it to be easily extended and customized. NRDP uses standard ports and protocols (HTTP(S) and XML) and can be implemented as a replacement for NSCA.[edit]
NSClient++This program is mainly used to monitor Windows machines. Being installed on a remote system NSClient++ listens to port TCP 1248. Nagios plugin that is used to collect information from this addon is calledcheck_nt. As NRPE, NSClient++ allows to monitor the so called "private services" (memory usage, CPU load, disk usage, running processes, etc.)Sumber : http://en.wikipedia.org/wiki/NagiosINSTALL NAGIOS
Now We Will Disable AppArmor
/etc/init.d/apparmor stopupdate-rc.d -f apparmor removeaptitude remove apparmor apparmor-utilsCreate Folder For Nagios And Nagios Plugins
mkdir /downloadsNow Let's Install The Required Programs For Nagios
Make sure you select Smarthost option when installing Postfix:aptitude -y install apache2 libapache2-mod-php5 build-essential libgd2-xpm-dev postfixNow let's update everything on this system:aptitude updateaptitude safe-upgradeNagios User Setup
useradd -m -s /bin/bash nagiospasswd nagiosusermod -G nagios nagiosgroupadd nagcmdusermod -a -G nagcmd nagiosDownload And Unzip Nagios And Nagios Plugins
cd /downloadswget http://prdownloads.sourceforge.net/nagios/nagios-3.2.3.tar.gzwget http://prdownloads.sourceforge.net/nagiosplug/nagios-plugins-1.4.15.tar.gztar -zxf /downloads/nagios-3.2.3.tar.gztar -zxf /downloads/nagios-plugins-1.4.15.tar.gzInstall Nagios
cd /downloads/nagios-3.2.3./configure --with-command-group=nagcmdmake allmake installmake install-initmake install-configmake install-commandmodemake install-webconfNagios Password
This is the password you will need to look at the nagios pages. If you install Nagios to a different directory please change this command to where the Nagios etc. folder will be.htpasswd -c /usr/local/nagios/etc/htpasswd.users nagiosadminEnter your password when prompted.Now we will restart Apache to make sure all of the changes take effect:/etc/init.d/apache2 restartInstall Nagios Plugins
cd /downloads/nagios-plugins-1.4.15/makemake installNow we need to make Nagios start at bootup:ln -s /etc/init.d/nagios /etc/rcS.d/S99nagiosChange Default Email Address For Nagios Admin
Open your favorite editor and open /usr/local/nagios/etc/objects/contacts.cfg and change this:nagios@localhost
To this:You@yourdomain.com
Once you have saved your changes to the contacts.cfg we need to verify that there are no errors in the configuration of Nagios./usr/local/nagios/bin/nagios -v /usr/local/nagios/etc/nagios.cfgHere is what you should see. It is okay to have a couple of warnings, but you can't have any errors. Now we are going to start nagios:/etc/init.d/nagios start
Now we are going to start nagios:/etc/init.d/nagios startPostfix Configuration For A Smarthost Relay
postconf -e 'relayhost=yourmailserver.com'postconf -e 'smtp_sasl_auth_enabled = yes'postconf -e 'smtp_sasl_password_maps = hash:/etc/postfix/sasl_passwd'postconf -e 'smtp_sasl_security_options ='echo "yourmailserver.com emailusername:emailpassword" > /etc/postfix/sasl_passwdNow we will need to change the password file attributes so only root has access to read it.chown root:root /etc/postfix/sasl_passwdchmod 600 /etc/postfix/sasl_passwdpostmap /etc/postfix/sasl_passwdNow we are going to set the map that will change your outbound messages from nagios to your email server username/email address.echo "nagios mailusername@yourmailserver.com" /etc/postfix/canonicalecho "canonical_maps = hash:/etc/postfix/canonical" >> /etc/postfix/main.cfpostmap /etc/postfix/canonicalNow we are going to restart Postfix:/etc/init.d/postfix restartNow that this all has been completed you can restart your system.Once your system has come back up you will be able to login to the website and look at your first Nagios installation.http://yourserver/nagios/Now login with the nagiosadmin username and password we created earlier: Now here is what you will see once you are logged in.
Now here is what you will see once you are logged in.
Installation Script For Nagios
Here is the installation script I have created to handle most of the work for installing Nagios. Please note the top of the script, you will need to define some of the variables for the installation to work correctly.#!/bin/bash # # AUTHOR : rbishop # DATE : 01.27.2011 # # PROG.-NAME : nagios-setup.sh # # FUNCTION : Installing Nagios on your System # # ####################################################################### ####################################################################### ## ## ## Configurable Settings for this Script
[edit]
sumber : http://www.howtoforge.com/nagios-installation-on-ubuntu-10.04-lucid-lynx-p3
Subscribe to:
Posts (Atom)


